Introduction
For some reasons, i made a .dmg image of a folder on my ✨ MacBook Pro M1 Pro ✨.
A DMG file is an Apple Disk Image file.
Nothing too complicated : to do so, I used Apple’s Disk Utility tool.
The encryption option got my interest and, only for testing purposes, I decided to create a small encrypted image and crack it in order to recover its content like an attacker would do… things didn’t go as I thought.
In this post, we will see step-by-step how complicated (not hard, complicated) it is for a non-Apple user to recover the content of an encrypted dmg file
what is shown in this post has been done on MacOS Sonoma 14.0, Windows 11 Parallels and Kali Linux.

Some knowledge about the DMG file extension and APFS 🤓
DMG is, as I said earlier, an Apple file extension.
It is used to distribute and install apps on MacOS.
They can contain data, softs, apps, a file system… many things.
DMG can also be used for compression and reduce space on a disk.
A MacOS user only need to double-click on a dmg file to open it / mount it as if it was an external drive.
Important point, a dmg image can be encrypted with AES 128-bit / 256-bit.
Disk Utility is a tool provided by Apple on MacOS systems to create and manage dmg files.
To finish with this part, I need to say that the dmg extension is associated with HFS+ and APFS.
These are file systems used by MacOS, APFS is the newer and was introduced in 2017 with MacOS Sierra.
For your knowledge, the main difference between these two FS is that APFS was introduced to optimize performances on SSDs and uses a Copy-on-Write system to contribute to data integrity.

Let’s create an encrypted dmg image 🔐
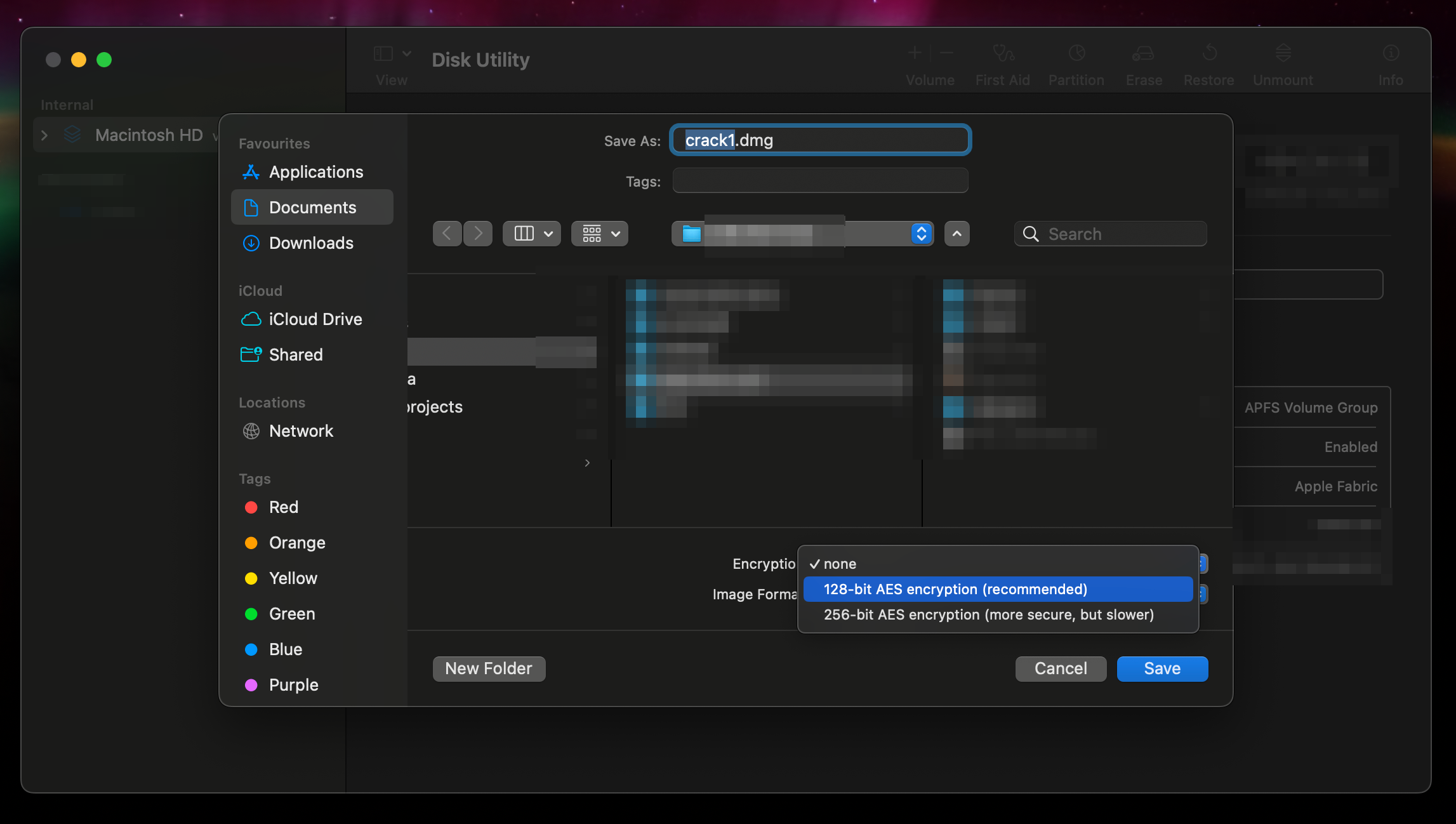
In order to illustrate what I want to show in this post, we’ll create an encrypted dmg file together 🎉.
Nothing too fancy :
- Open Disk Utility
- Select File > New Image > Image from folder
- Select a folder with something inside of it, it’s better
- In encryption, Select 128-bit AES
- Enter a password (please don’t forget it…)
- Done, you are now a hacker 🤡
Attaquons 🤺
Now, let’s imagine that, as a skiddy, you intercepted an encrypted dmg file.
Let’s try to recover its content !
Because it would be too simple and that it is the purpose of this post, we will run the attack without using MacOS.
Indeed, dmg images have been made for MacOS…
From now, we will play as if we had no knowledge on what we have except the extension.
What do we have here ?
We’ll start the investigation from Linux.
Running the file command will not be useful.
If you google “dmg on linux” (on Startpage 🤓), you will find that 7-zip is able to uncompress a dmg file… Perfect !
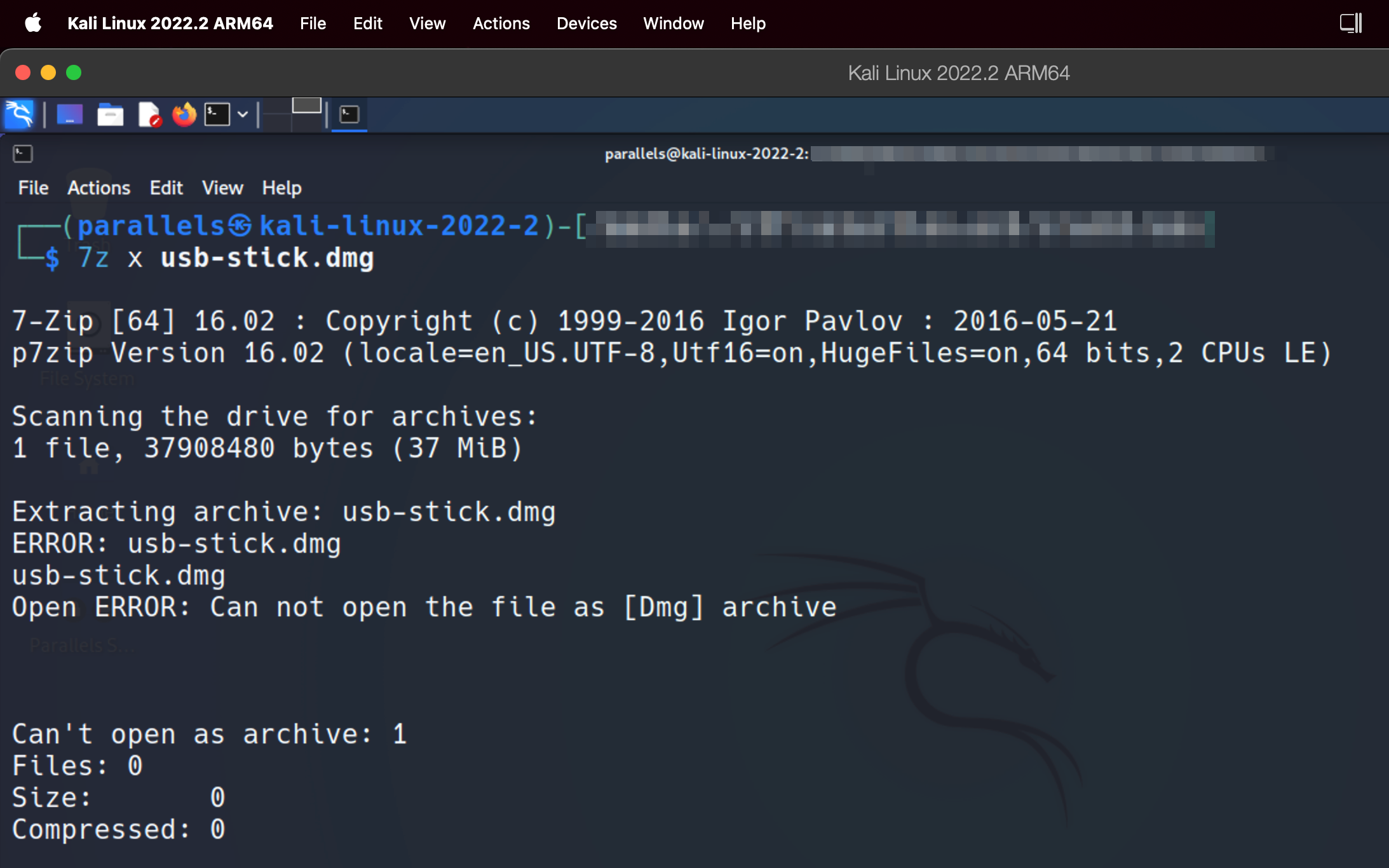
Actually, it’s not that simple.
What I like to do in that case is to put the file in HexEdit.
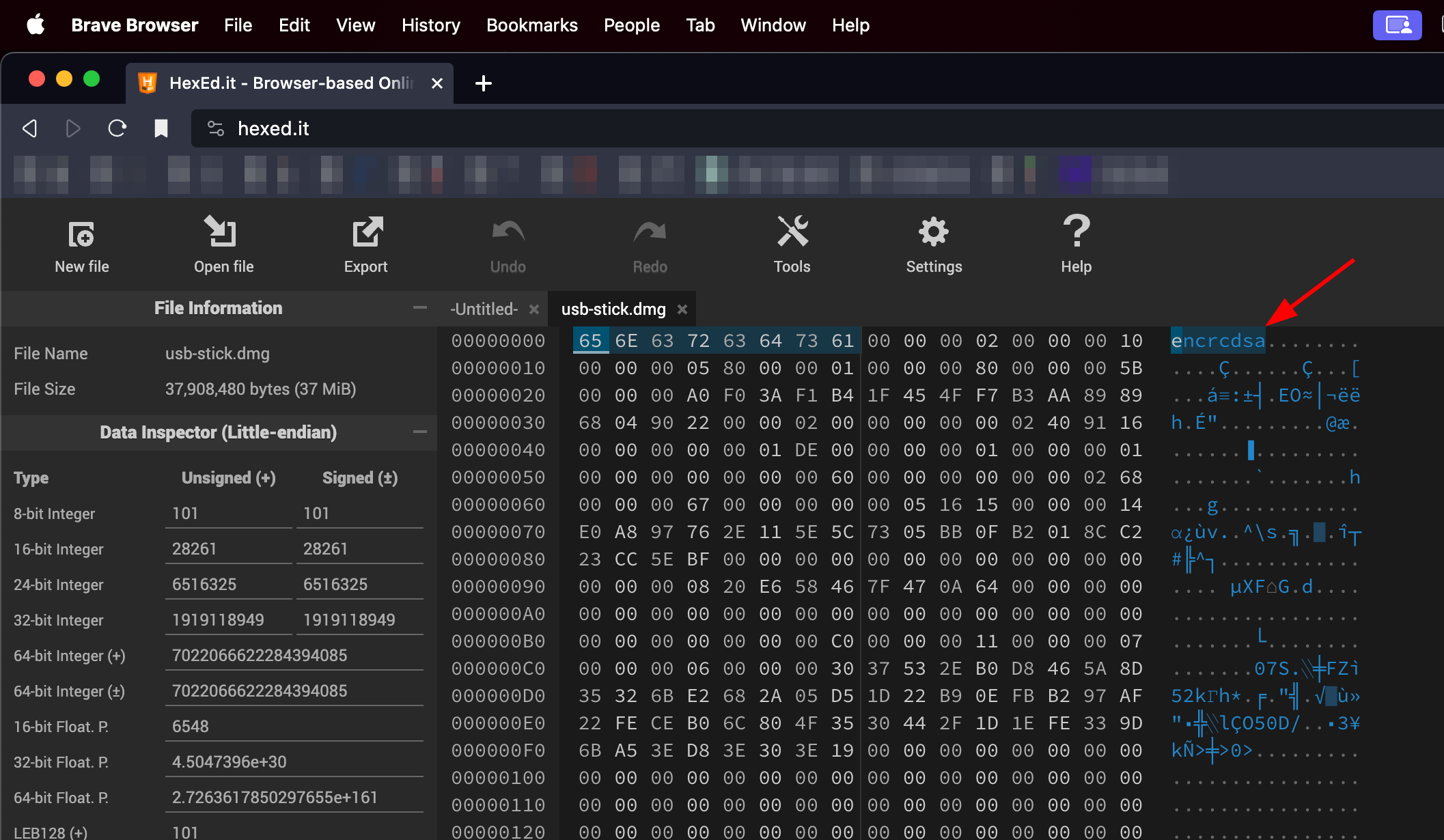
We can see that the file starts with the “encrcdsa” sequence, meaning that the file is encrypted.
After some researchs, I found that 7-zip is unable to deal with encrypted dmg files… 😔
What can we do then ? Is it the end for us ? Where skills ?
Let’s crack it
What would we do if we had an encrypted zip file and wanted to crack it ?
Let’s ask our common friend John The Ripper.
John is able to attack the hash of our dmg’s password.
For testing purposes, we will write into a fake wordlist the password we chose to encrypt our dmg image. The idea of this post isn’t to learn how to brute force attack an encrypted file.
To do so :
dmg2john image.dmg > outputjohn --wordlist=wordlist.txt output
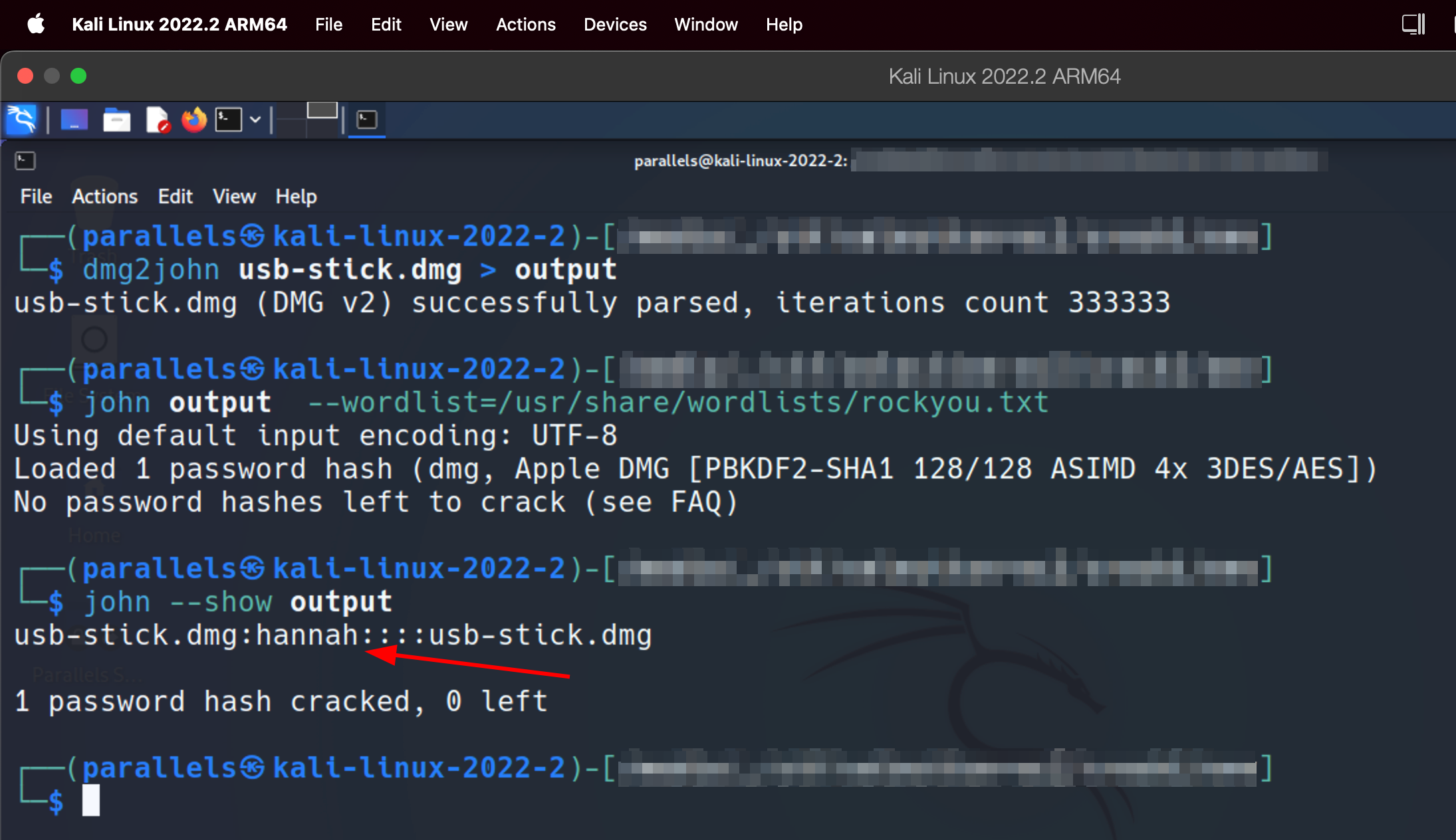
GG, you are now a hacker ! 🤡
Let’s (try to) open it
Well well well… we now have the password used to encrypt the image but we’re still unable to open it…
Of course, we could just use MacOS but as a skiddy attacker, we’ll suppose that we don’t have a MacOS device on hand.
I tried many things before understanding that it won’t be possible to open an encrypted dmg image on Linux… but why ?
The reason is pretty simple, APFS still isn’t 100% compatible with Linux.
There are some drivers like apfs-fuse but I wasn’t able to make it work with my encrypted dmg and as far as I know, there isn’t any other driver available.
Indeed, propriertary file systems like APFS depends on reverse engineering.
To be honest, I wasn’t able to find anything working on Linux to open my dmg image. It’s kind of frustrating to have the password and not be able to open it !
For this reason, I decided to call an old friend… someone I don’t like to stay with except when I need to attack him…

If the Linux community didn’t create a stable APFS driver, maybe the Windows community did 😂 (spoiler alert : they did actually).
I tried different tools, some looked like spywares, some asked for money in order to decrypt my image but… anyway.
I didn’t find any program able to open my encrypted dmg image 🤦🏻♂️.
I chose to dig into github and I found dmg2img.
The idea is to convert the encrypted dmg image into a decrypted .img. Thus, maybe I’ll have some more options to read its content.
I cloned the repo on Windows but, because life isn’t easy, it didn’t work on my image : I didn’t find any flag to deal with encryption.
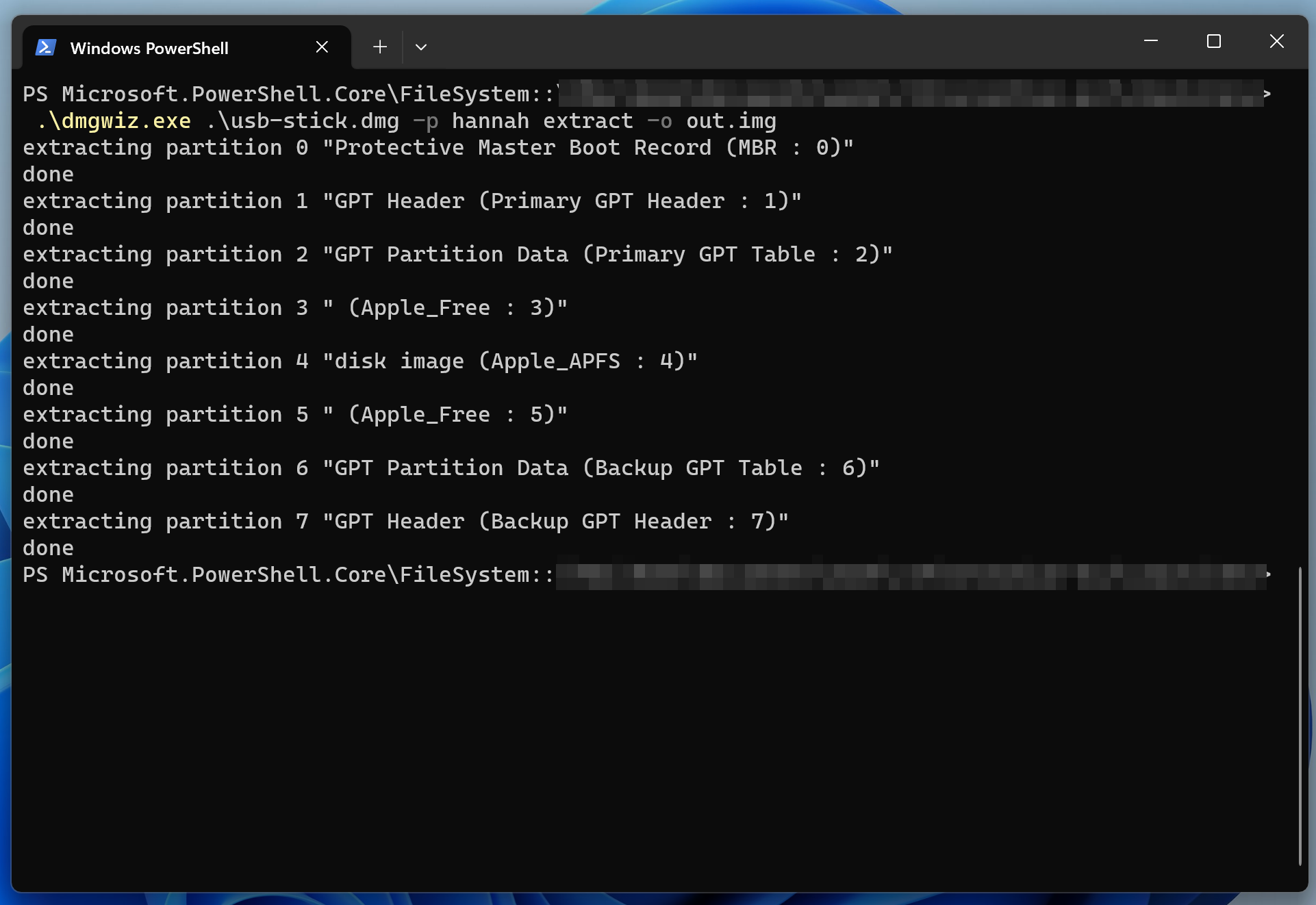
Thanksfully, I found another script called DmgWiz which is a dmg2img’s clone with more features and written in Rust.
I used it on my file and… ENFIN CA FONCTIONNE 🎉 :
Here is the command I entered in Windows Terminal :
.\dmgwiz.exe .\image.dmg -p <password> extract -o out.img
Let’s open it
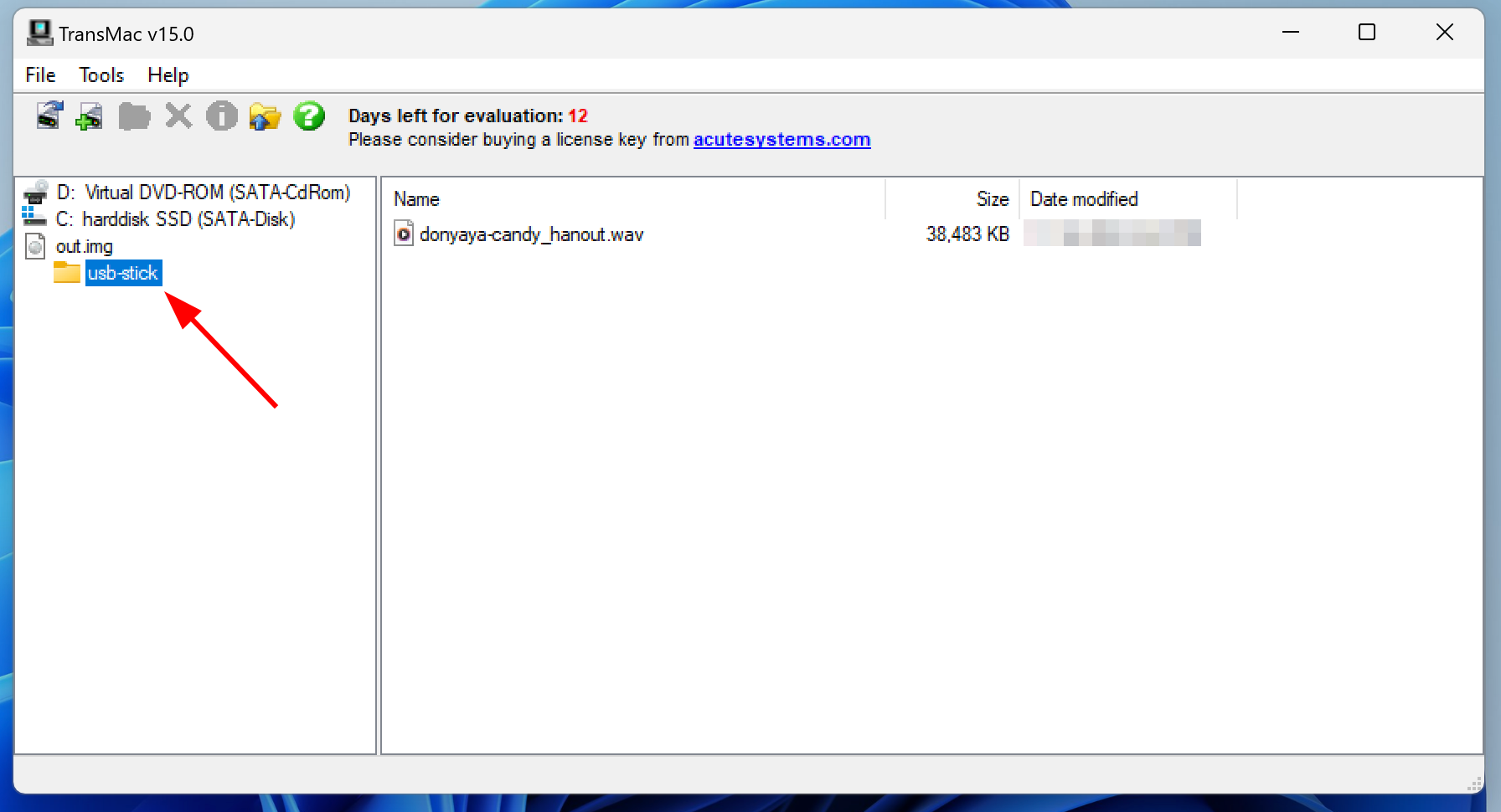
Ok ! We now have a decrypted .img file under APFS.
Before trying to open it with apfs-fuse again, maybe Windows has something to offer ?
YES, the only software on Windows that allowed me to open my image is TransMac.
The only problem with it is that it runs for 15 days from installation to allow user evaluation.
Conclusion
I wrote this post because it is too complicated (not hard, complicated) to deal with an encrypted dmg image on another OS than MacOS.
Judging by Apple’s philosophy, it actually is a great thing : you need to buy their device to avoid installing a paid third-party software to open an encrypted dmg file.
I hope you found this post useful, and / or gave you some ideas.
I think giving an encrypted dmg image in a CTF could be a cool idea :).
To sum up
To crack and open an encrypted dmg image, I needed to :
-
First, on Linux (or Windows)
dmg2john image.dmg > outputjohn --wordlist=wordlist.txt output
-
Then, on Windows
- Download dmgwiz.exe
- Run
.\dmgwiz.exe .\image.dmg -p <password> extract -o out.imgin Terminal - Open out.img image with TransMac
- Done !
-
What we would have done on MacOS :
- Crack it with john
- Double click on the dmg image and enter the password…